Updates:
- Originally posted on Oct 22 2016 as “The Ongoing Ethereum Attacks (Work In Progress)”, but renamed after finding the links to the mining pools.
- 05:55 Oct 23 2016 UTC – First estimate of the number of accounts created by the SUICIDE opcode is 19,041,840 by retrieving the information from Parity. The original estimate was manually computed by viewing the transactions in etherscan.io, which did not pick up most of the empty accounts. Compare to 777,647 real accounts. That’s why your syncing has been taking such a long time.
- 13:48 Oct 25 2016 UTC – added further analysis by /r/Jey_s_TeArS to the bottom of the Summary section.
- 21:47 Oct 25 2016 UTC – added comment by /r/DwarfPool to the bottom of the Summary section.
Table of contents
- Summary
- The First Wave Of Attacks
- The Second Wave Of Attacks
- Bingo!
- The Ethereum Classic And The DAO Hacker Connection
- Coordinated Spam Or Lone Operative
Summary
The Ethereum network has been undergoing a series of attacks since the Devcon2 Ethereum Developers Conference on Sep 18 2016. The Ethereum network activated a hard fork on Oct 19 2016 that successfully stopped the spam transaction attack. Less than a day after the hard fork, a new wave of attacks was executed by the attacker, but these attacks have had less impact on the Ethereum network.
The attacks have now ceased, for the moment at least. The attacker may have given up as the second wave of attacks have had little impact on the network.
The attacker’s transactions have been anonymous until now. The tracing of the transactions below eventually led to the transactions showing that the attacker has used the services of the EthPool and DwarfPool mining pools. These mining pool transactions could reveal the attacker’s IP address, assuming none of the accounts involved have had their private keys stolen.
Whether anyone will pursue the attacker is unknown at this point in time. The attacker could be the same USD 50 million The DAO hacker, or someone who wants us to think that. Some of the attacking accounts donated a few Classic ethers (ETC) to the Ethereum Classic development account, the same account The DAO hacker contributed 1,000 ETCs to when they had access to their booty. And both attackers made the same measly order of donation to the Ethereum Classic development fund.
One positive aspect of these attacks is the improvement of the security of the Ethereum network while still in it’s early phase.
Overall, the Ethereum network kept on chugging along despite the repeated attacks. Many nodes crashed in the first attack, but due to the diversity in node clients, the network continued running. With the spam transaction attacks, node clients were slowed down especially nodes with limited RAM and non-solid state storage. With the many millions of empty account attack, node clients were slowed down further. Users had trouble syncing their full node wallets. Transactions could not be submitted with normal fees – some transactions fees were raised up to 45x the normal fee as this prioritises the transactions. Large smart contracts could not be deployed as the miners were advised to lower the gasLimit to reduce the effects of the spam transactions. Some miners started mining blocks with zero transactions for fear of slowing down their nodes. But the network kept on chugging along and hopefully will continue to do so. A very nice resilient network decentralised over 7483 nodes.
Update 13:48 Oct 25 2016 UTC – User /r/Jey_s_TeArS on the reddit post Ethereum Network Attacker’s IP Address Is Traceable writes:
Click here for /r/Jey_s_TeArS's "quick analysis".Following the quick analysis I made on the way back from Shanghai I was pointing to an address almost empty now and was initially funded by a tx from shapeshift among other tx from shapeshift: https://etherscan.io/tx/0xc6b62e729b7ce0cb2f919fe2e015404e99bc6077dfef55846272069a38538b97 I have been harassing the customer service of shapeshift and obtained this two BTC tx used to fund some of the attackers address http://btc.blockr.io/tx/info/64793d565a20564731671d3ec454fac227f9a709ac278816664a518d3efdcf98
http://btc.blockr.io/tx/info/8553e73063d695162866557b773b5fbc4f325a5dd2157543e88691f534997c10If you care to carry on investigating let me know if I can be of any help.
The contract involved : https://etherscan.io/address/0xd6a64d7e8c8a94fa5068ca33229d88436a743b14
edit bis: looks like the attack is now (2315287) slowing down last tx to the contract involved was made 1 hours ago . Some the adresses listed below also interacted with what looks like a copy of the attacking contract https://etherscan.io/address/0x0c40cf6dd1b74c6edfc4729021a11f57b31e3c27
edit bis bis Tx to the contract are now (2318227) going fast and with low fees (0.006) but multiple attacking transactions get included in blocks see https://etherscan.io/txs?block=2318227&p=2
The current fee for the DoS tx seems to be settled now at 0.027 eth. If a tx is included in a block every 15 sec, this attack is costing 6.48 eth per hour or 155.52 eth per day. At 2312624, the sum of the balances of the addresses calling the contract (see below) is 150 eth, so expect at least 24 hours of trouble.
edit: I guess due to the pools and miners adapting their gaslimit and gasprice the tx fee of the attacker is now up to 0.03465 (+28%)
The Contract creator: https://etherscan.io/txs?a=0x0c35a2e957e8f88027bc7b2779b9f95f0848992d&p=3 Note that this address has created a lot of similar contracts 6 days ago between block 2271721 and block 2272038 and resumed creating contract 4 days ago at 2282288 to 2283381 This address is almost empty now and was initially funded by a tx from shapeshift: https://etherscan.io/tx/0xc6b62e729b7ce0cb2f919fe2e015404e99bc6077dfef55846272069a38538b97
There are 15 addresses related to the contract so far (analysis done at 2312453 ) and 1 address (a contract) that received a transaction from it. You can watch it on : https://live.ether.camp/account/d6a64d7e8c8a94fa5068ca33229d88436a743b14/stat
There are 10 address calling the contract that have the same pattern of creation, those addresses where all loaded from Poloniex between 2300996 and 2301016 :
https://etherchain.org/account/0xe8F64922aA2B868A1C9ee4E43FA6ed673A65b940#txreceived
https://etherchain.org/account/0x853f9F86691b5f7175Ae47D2741dd29703C0024d#txreceived
https://etherchain.org/account/0x299809a293CBfEB3D077560847888e3770B51D3B#txreceived
https://etherchain.org/account/0x3e1c8Cac809d4E22B44b5Fb8a8491B9Db94aB045#txreceived
https://etherchain.org/account/0x66918bAef5Acf0c412AC41BA447d458939D3D176#txreceived
https://etherchain.org/account/0x06ac9e25a76fe5cf7df0a19c29dfdc900003d0c6#txreceived
https://etherchain.org/account/0xf9110f7f0191317eb4bcd96e80d86946eb5426c5#txreceived
https://etherchain.org/account/0xb2d7b6108d8d6f3c521f7321f5c299c638ed4e9b#txreceived
https://etherchain.org/account/0x9851131b33fd9e084c56fb4a341460e8ea23e737#txreceived
https://etherchain.org/account/0x166afb934f8e852ccfed857245305005c4673fc4#txreceived
This address was funded multiple times (all initially from shapeshift) and is also calling the contract: https://etherscan.io/txs?a=0xCa018d88926497c0468a8a06DFd3732CC7827b2c&p=3
There is only one address that received something from the contract: https://etherscan.io/address/0x47b39d9ab2b170fef87705b92988f919503c28b0 Note that this is a contract created by the same person (0x0c35a2… ) 5 days ago at 2282288
Furthermore those 3 addresses are also related to the contract and probably used for testing, receiving funds 6 days ago around bloc 2278648 :
https://etherchain.org/account/0x29446e8d2f0ca2e7fd9e46665e80fc2cd55bf262#txreceived
https://etherchain.org/account/0x0c35a2e957e8f88027bc7b2779b9f95f0848992d#txsent
https://etherchain.org/account/0xab90c4455d32f1e579152f52377e3cbf9b3cc37b#txsent
This “testing addresses” lead to this contract address : https://etherscan.io/address/0x45FAeC35E32676568ad827AEa17FB7431EF390bC the address that created currently used contract (0x0c35a2e…) interacted with it.
Update 21:47 Oct 25 2016 UTC – User /r/DwarfPool on the reddit post Ethereum Network Attacker’s IP Address Is Traceable writes:
IP addresses are known a long time ago, I write also to ethcore-team ISP of attackers. But how can it help?
Update 01:18 Oct 22 2016 UTC – A Perl script and the raw data for the 6 known offensive contracts is available in github.com/bokkypoobah/EthereumNetworkAttackData.
Posted on reddit/r/ethereum – The Ongoing Ethereum Attacks (Work In Progress) and Hacker News.
The First Wave Of Attacks
The first attack started on block #2,283,416 at Sep-18-2016 06:04:56 PM +UTC (01:04:56 Sep 19 Shanghai time) and targeted the go-ethereum geth clients, causing a memory error and shutting down these nodes across the network. Part of the design of the Ethereum network is the diversity of node clients. While geth (implemented in Go) crashed, Parity (implemented in Rust) and EthereumJ (implemented in Java) kept the network running.
geth – From Shanghai, with love (v1.4.12) was released on Sep 19 with the these code change.
The Offensive Transactions
The offensive transactions were both:
- geth memory crash transaction – tx 0x5c19…6e82 in #2,283,416 @ Sep-18-2016 06:04:56 PM +UTC from 0x1d0fee96aa9750f87894b034d25e17edca8b76a3 to contract 0xb284e6a25d0972f9a92fec45d2075067db2d49b0
- Spam DoS transaction – tx 0x7bf5…3455 in #2,283,416 at Sep-18-2016 06:04:56 PM +UTC from 0x0c35a2e957e8f88027bc7b2779b9f95f0848992d to contract 0xd6a64d7e8c8a94fa5068ca33229d88436a743b14
The geth Memory Crash Contract
The geth memory crash contract 0xb284e6a25d0972f9a92fec45d2075067db2d49b0:
- Was created in tx 0x403b…b887 in #2,283,397 at Sep-18-2016 05:56:48 PM +UTC from 0x1d0fee96aa9750f87894b034d25e17edca8b76a3
- Sent 9 transactions:
- First tx 0x0e40…f4c2 in #2,283,405 at Sep-18-2016 05:59:17 PM +UTC
- geth memory crash trigger tx 0x5c19…6e82 in #2,283,416 at Sep-18-2016 06:04:56 PM +UTC
- Last tx 0x83f9…9363 in #2,301,372 at Sep-21-2016 05:08:37 PM +UTC
- The list of accounts sending the transaction are:
The Spam DoS Transaction Contract
The spam DoS transaction contract 0xd6a64d7e8c8a94fa5068ca33229d88436a743b14:
- Was created in tx 0x2109…05bc in #2,283,249 at Sep-18-2016 05:18:59 PM +UTC from 0x0c35a2e957e8f88027bc7b2779b9f95f0848992d
- Sent 6830 transactions:
- First tx 0x7bf5…3455 in #2,283,416 at Sep-18-2016 06:04:56 PM +UTC
- Last tx 0x0b97…e7d4 in #2,379,641 at Oct-04-2016 04:46:37 PM +UTC
- The list of MANY accounts sending the transaction include:
- 0x0c35a2e957e8f88027bc7b2779b9f95f0848992d. This was funded from ShapeShift2 in tx 0xc6b6…8b97 at Sep-08-2016 02:08:32 PM +UTC
- 0x1248d79bdebd516156930a5c8ee232d4ed80ead4. This was funded from Poloniex in tx 0xc422…ca39 at Sep-21-2016 03:51:18 PM +UTC
- 0x1fa0e1dfa88b371fcedf6225b3d8ad4e3bacef0e. This was funded from 0x1ff804d8e15d54dc44793269b7749c36c775cb56 at Oct-01-2016 01:58:01 AM +UTC, which was funded from Poloniex in tx 0x7eff…7855 at Sep-21-2016 09:54:26 PM +UTC.
- 0x29446e8d2f0ca2e7fd9e46665e80fc2cd55bf262. This was funded from ShapeShift in tx 0x53c3…987e at Sep-17-2016 11:00:54 PM +UTC
- 0x3e1c8cac809d4e22b44b5fb8a8491b9db94ab045. This was funded from Poloniex in tx 0xece…15f1 at Sep-21-2016 03:49:32 PM +UTC
- 0x40525ac2fe3befe27a4e73757178d4accfef71da. This was funded from 0x1ff804d8e15d54dc44793269b7749c36c775cb56 at Oct-01-2016 02:11:03 AM +UTC, which was funded from Poloniex in tx 0x7eff..7855 at Sep-21-2016 09:54:26 PM +UTC.
- 0x66918baef5acf0c412ac41ba447d458939d3d176. This was funded from Poloniex in tx 0x22c2…6bfd at Sep-21-2016 03:49:04 PM +UTC
- 0x853f9f86691b5f7175ae47d2741dd29703c0024d. This was funded from Poloniex in tx 0xe9b1…b45a at Sep-21-2016 03:48:12 PM +UTC
- 0xab90c4455d32f1e579152f52377e3cbf9b3cc37b. This was funded from ShapeShift in tx 0x518c…eae5 at Sep-17-2016 10:45:54 PM +UTC
- 0xca018d88926497c0468a8a06dfd3732cc7827b2c. This was funded from ShapeShift in tx 0xc650…ac09 at Sep-17-2016 10:42:28 PM +UTC
- 0xd3e32594cedbc102d739142aa70d21f4caea5618. This was funded from 0x1ff804d8e15d54dc44793269b7749c36c775cb56 at Oct-01-2016 02:11:03 AM +UTC, which was funded from Poloniex in tx 0x7eff..7855 at Sep-21-2016 09:54:26 PM +UTC.
- 0xde21bc367afe7a3705a15255ff46a5ae91e8341c This was funded from 0x1ff804d8e15d54dc44793269b7749c36c775cb56 at Oct-01-2016 02:11:03 AM +UTC, which was funded from Poloniex in tx 0x7eff..7855 at Sep-21-2016 09:54:26 PM +UTC.
- 0xe8f64922aa2b868a1c9ee4e43fa6ed673a65b940. This was funded from Poloniex in tx 0x2a88e275 at Sep-21-2016 03:48:29 PM +UTC
- 0xf9110f7f0191317eb4bcd96e80d86946eb5426c5. This was funded from Poloniex in tx 0x2eb8…f0ef at Sep-21-2016 03:51:04 PM +UTC
- Has the following opcodes (only the beginning shown), showing the offensive EXTCODECOPY opcode:
1234567891011121314151617181920212223242526272829303132PUSH2 0x2800PUSH1 0x00DUP1PUSH20 0x4ce312538aa0b69740cbabfbfd8a2a8e628f660dEXTCODECOPYPUSH1 0x00JUMPDESTDUP1MLOADPUSH13 0x01000000000000000000000000SWAP1DIVPUSH20 0x66726f6d7368616e67686169776974686c6f7665SWAP1XOREXTCODESIZEPOPPUSH1 0x14ADDDUP1PUSH2 0x2800EQISZEROPUSH2 0x001eJUMPIPOPPUSH2 0x2800PUSH1 0x00DUP1PUSH20 0x89ad4426e629368ecb9d63ab01e5ca538fbdc1a4EXTCODECOPY...
The Account Bloat Attack
The attacker sent low cost transactions to create many millions of empty accounts on the Ethereum blockchain, slowing down the processing of the Ethereum node clients.
Update 05:55 Oct 23 2016 UTC – First estimate of the number of accounts created by the SUICIDE opcode is 19,041,840 by retrieving the information from Parity. The original estimate was manually computed by viewing the transactions in etherscan.io, which did not pick up most of the empty accounts. Compare to 777,647 real accounts. That’s why your syncing has been taking such a long time.
User /u/arrnx on the reddit post The Ongoing Ethereum Attacks (Work In Progress) provided two address involved in the creation of the many millions of empty accounts:
- SUICIDE empty account creator contract – 0x6a0a0fc761c612c340a0e98d33b37a75e5268472. This contract was created in tx 0x0b72…029f from 0x1fa0e1dfa88b371fcedf6225b3d8ad4e3bacef0e, which was funded from Poloniex and is traced above. This contracts:
- First tx 0x0f5d…1a7e in #2,421,507 at Oct-11-2016 03:55:16 PM +UTC
- Last tx 0x3c37…6a785 in #2,435,148 at Oct-13-2016 10:36:09 PM +UTC
- Has 4751 transaction executed against it, 1 for the creation and 4750 to execute the offensive code.
- Of the 4750 transaction, 4746 generated 500 empty accounts each and the last 4 ran out of gas and only generated 121 empty accounts.
- In total ~ (4 x 121) + (4,746 x 500) = 2,373,484 empty accounts were created.
- Here’s one of the 500 empty account creation transaction listing:
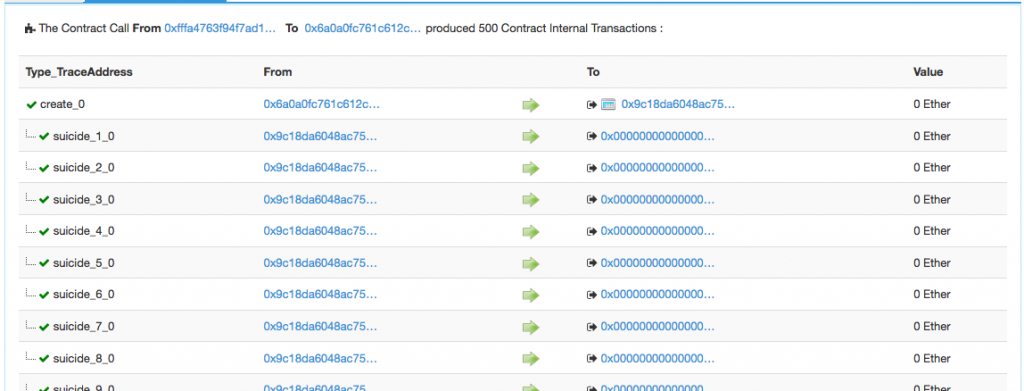 And here’s one of the empty accounts created:
And here’s one of the empty accounts created:
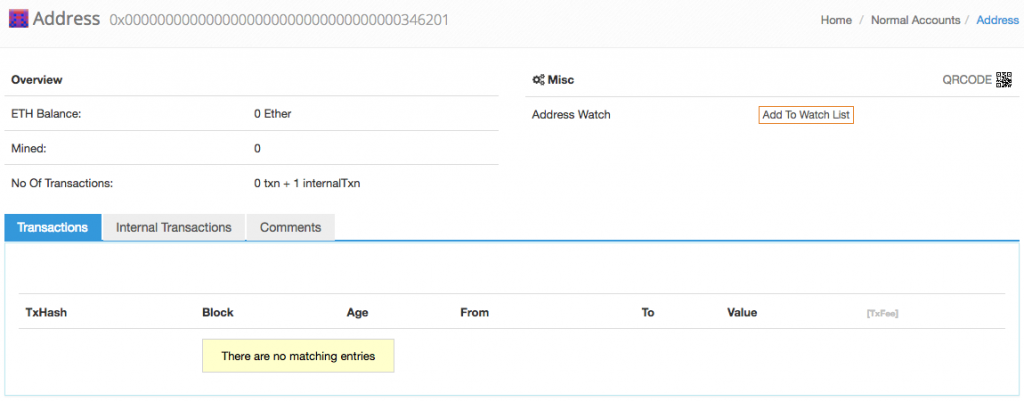
- CREATE empty account creator contract – 0x7c20218efc2e07c8fe2532ff860d4a5d8287cb31. This contract was created in tx 0xc590…5b2d in #2,423,558 at Oct-12-2016 12:16:02 AM +UTC from 0xfcd004fbad7e8ffee821d8a10d7f0685b14933b1, which was mined 434 days ago and is traced below.
- First tx 0x462f…6de7 in #2,423,577 at Oct-12-2016 12:20:16 AM +UTC
- Last tx 0xd595…4811 in #2,463,130 at Oct-18-2016 01:50:28 PM +UTC
- Has 34,149 transactions executed against it, 1 for creation and 34,148 to execute the offensive code
- Each of the 34,148 transactions created an empty account.
- Here’s one of the creation transaction:
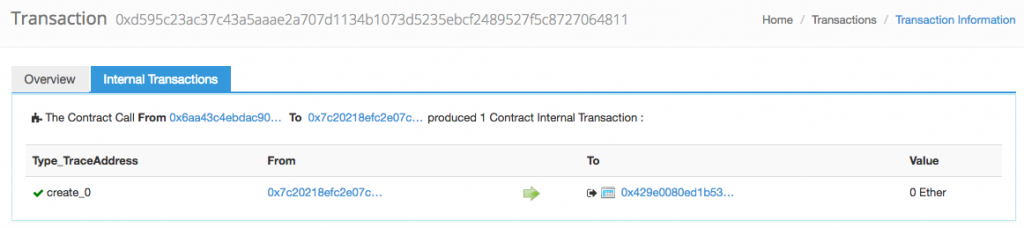 And here’s one of the empty accounts created:
And here’s one of the empty accounts created:
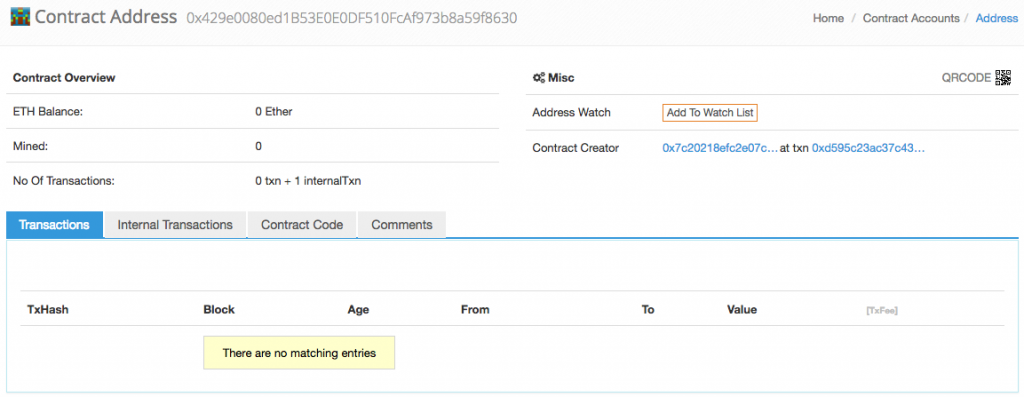
- A total of ~2,373,484 + 34,148 = 2,407,632 empty accounts were created. This is what the next state bloat hard fork intends to clean up.
The Gas Reprice Hard Fork
geth – Note 7 (v1.4.18), Parity v1.3.8, ethereumj v1.3.6 and Ethereum Wallet/Mist v0.8.6 activated a Gas Reprice hard fork on #2,463,000 at Oct-18-2016 01:19:31 PM +UTC rendering the spam DoS transactions above obsolete.
The Second Wave Of Attacks
As reported in Lol, I think its another attack contract – Burns fees like a champ. Somone is very persistent here 🙂, a new wave of attacks commenced less than a day after the Gas Reprice hard fork involving the two following contracts:
The Second Wave – The First Contract
The contract 0xbd37ee00e47c0fe0def80bd95c498698b4a15235:
- Was created in tx 0x4ac5…f334 in #2,468,199 at Oct-19-2016 09:38:25 AM +UTC) from 0xfcd004fbad7e8ffee821d8a10d7f0685b14933b1. The ethers from this account were mined over 434 days ago.
- Sent 868 transactions:
- First tx 0x0438…276b in #2,468,209 at Oct-19-2016 09:42:42 AM +UTC
- Last tx 0xfe13…de9d in #2,468,823 at Oct-19-2016 12:22:11 PM +UTC
The Second Wave – The Second Contract
The contract 0xb6389d6575966f946e190b9d538c3259857ed2c7:
- Was created in tx 0xc590…5b2d in #2,468,662 at Oct-19-2016 11:36:21 AM +UTC from 0xfcd004fbad7e8ffee821d8a10d7f0685b14933b1. The ethers from this account were mined over 434 days ago.
- Sent 7494 transactions:
- First tx 0x06c7…19b0 in #2,468,687 at Oct-19-2016 11:41:53 AM +UTC
- Last tx 0x0203…3c01 in #2,474,792 at Oct-20-2016 12:27:05 PM +UTC
The reason why this stopped ?temporarily is because all the accounts including 0xfcd004fbad7e8ffee821d8a10d7f0685b14933b1, 0x3318183894290cfa67e3c76767183ae4e8cd2ad3, 0x8e3d6a8496cbac7ea255fe35be5d8e03a419c71a and 0xcc2c2cd417a9c39cf0e48622988dbec0b1b37064ran out of ethers, and the attacker must be asleep.
Bingo!
The account 0x3318183894290cfa67e3c76767183ae4e8cd2ad3 was funded in tx 0xe9e5…5d0e at Oct-12-2016 11:07:27 PM +UTC from 0xc16721bd742d54b19a49425a91cb06db6d112dbc:
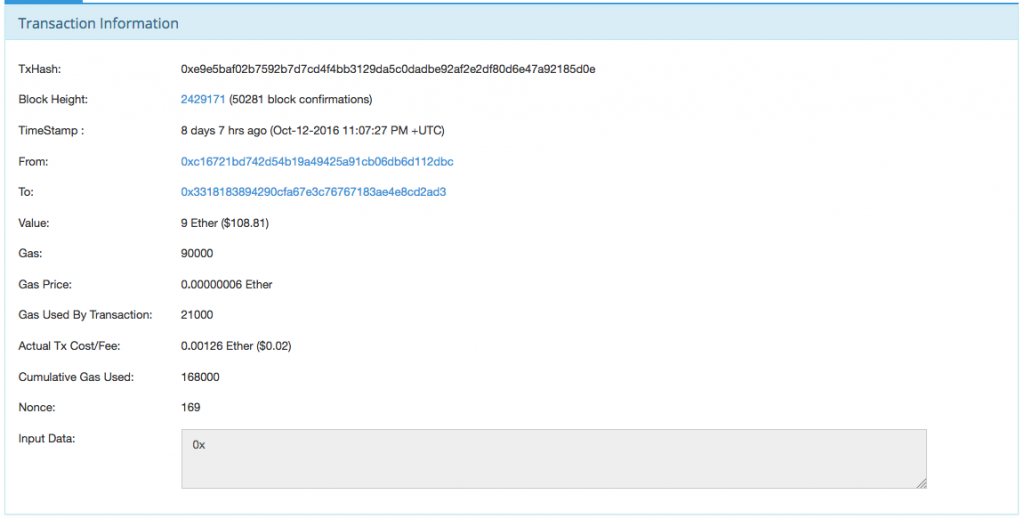 Account 0xc16721bd742d54b19a49425a91cb06db6d112dbc was funded in 0x45b4…701c at Oct-12-2016 07:26:30 PM +UTC from 0xba0577e1419237fd4b8c14a6f49984f6466b5996:
Account 0xc16721bd742d54b19a49425a91cb06db6d112dbc was funded in 0x45b4…701c at Oct-12-2016 07:26:30 PM +UTC from 0xba0577e1419237fd4b8c14a6f49984f6466b5996:
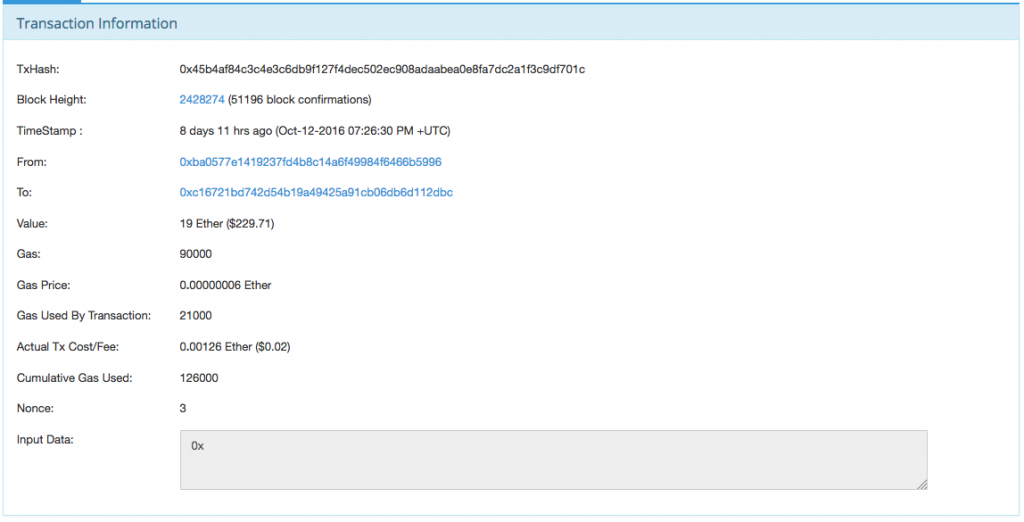 Account 0xba0577e1419237fd4b8c14a6f49984f6466b5996 was funded from Ethpool in tx 0xb266…89bf at Aug-09-2015 12:17:46 AM +UTC and DwarfPool1 in tx 0x1f0b…c404 at Mar-08-2016 03:36:49 AM +UTC many times until tx 0x5468…20e5 at May-26-2016 06:06:47 PM +UTC:
Account 0xba0577e1419237fd4b8c14a6f49984f6466b5996 was funded from Ethpool in tx 0xb266…89bf at Aug-09-2015 12:17:46 AM +UTC and DwarfPool1 in tx 0x1f0b…c404 at Mar-08-2016 03:36:49 AM +UTC many times until tx 0x5468…20e5 at May-26-2016 06:06:47 PM +UTC:
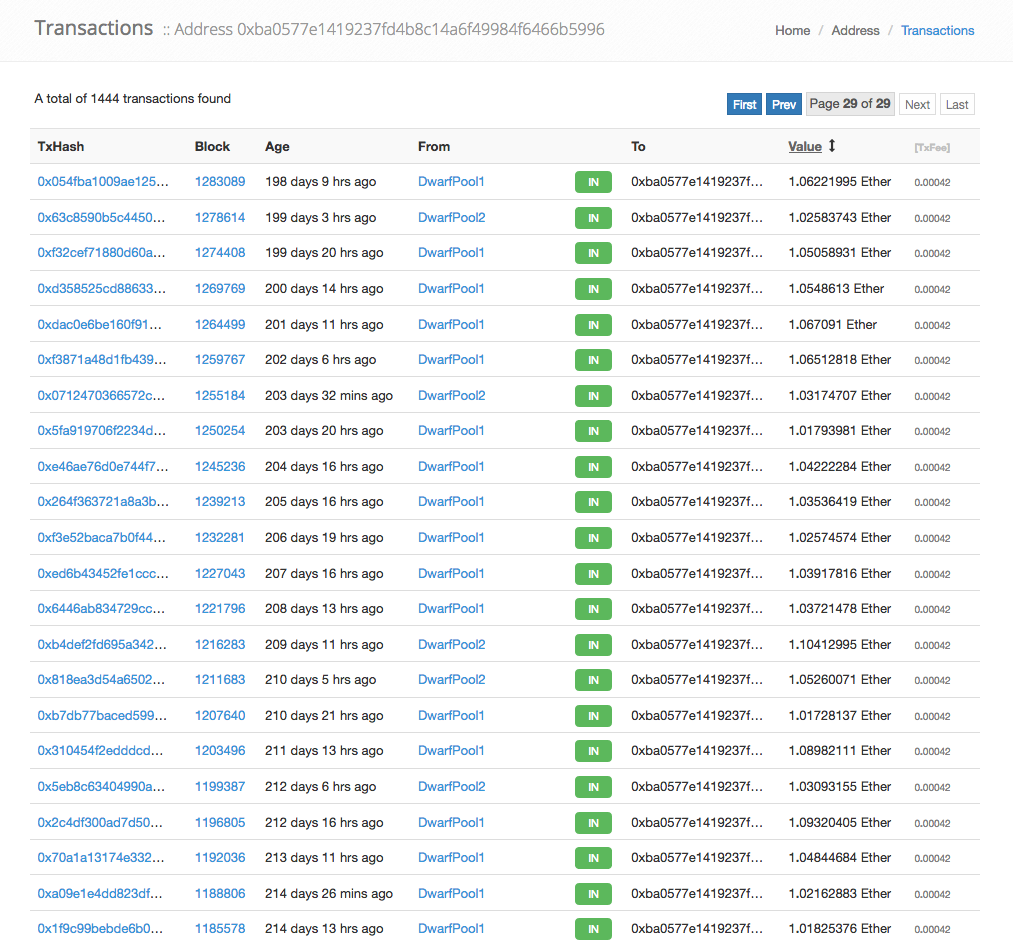
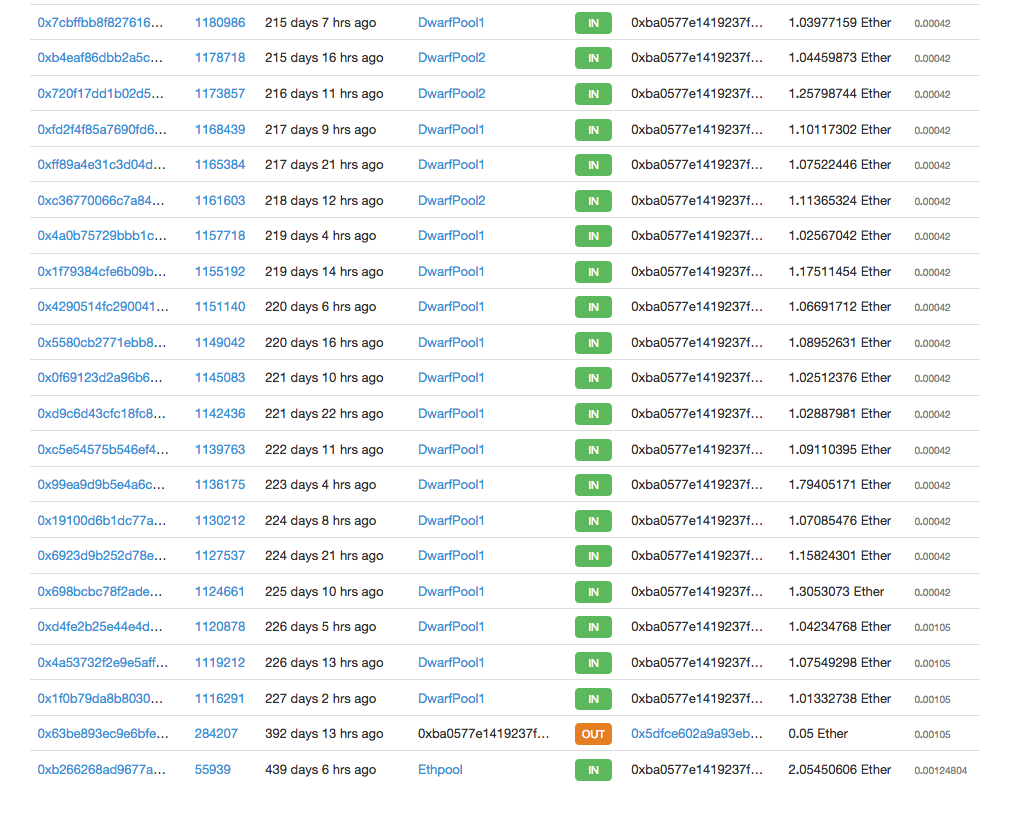 Some of these pools require IP addresses that the miner is mining from to confirm the miner’s credentials.
Some of these pools require IP addresses that the miner is mining from to confirm the miner’s credentials.
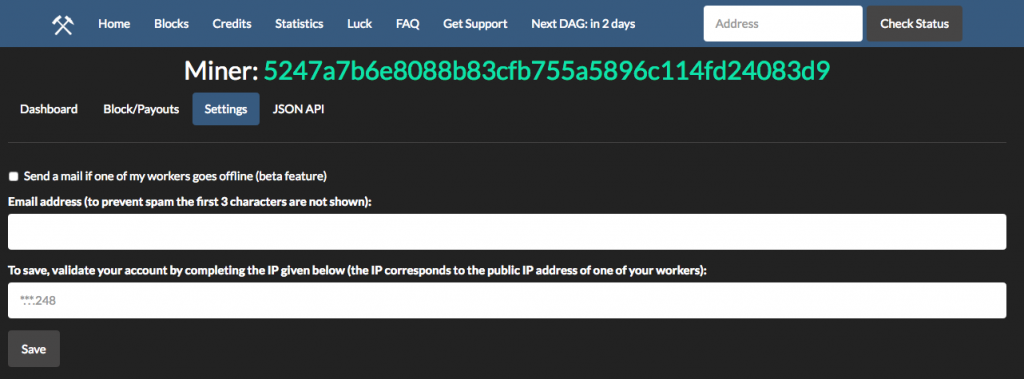
EthPool requires IP address confirmation for change in account setting, and stores the miner’s IP address and would therefore have an association between the miner’s account and IP address:
And here is the attacker’s statistics from DwarfPool:
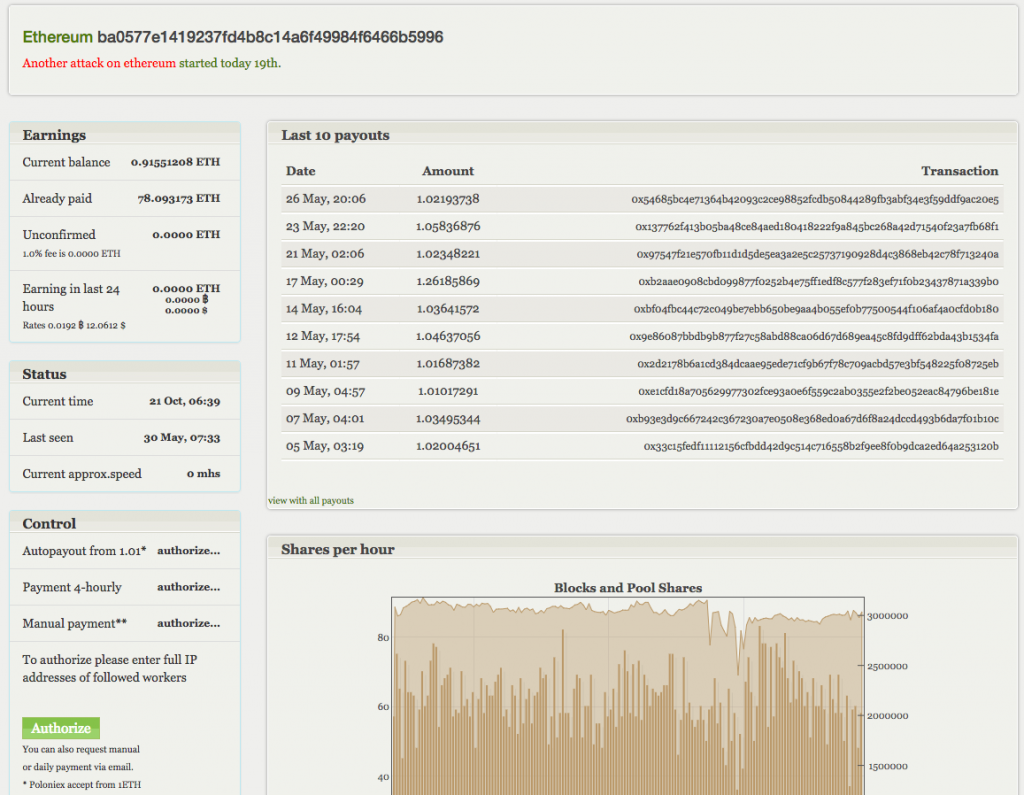
The attacker earned around 26 ETH mining at DwarfPool in April 2016. This is the equivalent of about 125 Mhs, or 4 x R9 390X GPUs (my 125 Mhs solo miner earned 5 blocks or ~ 25 ETH in the same period):
User /u/tsunamiboy6776 asked on First Ethereum hard fork successful; second imminent “How could the ip be used? Couldn’t be using a proxy or vpn?”.
The attacker could use a proxy, VPN or ?TOR to hide their IP address, but it is highly unlikely they would have done so. It is far easier to hide the association between your IP address and your Ethereum mining rewards account just by solo mining. And this pool mining was conducted before the idea of The DAO was floated, with the juicy USD 50 million bug in the code. The attacker could have planned these attacks well in advance, but why would they bother pool mining if they could just solo mine anonymously with higher profitability compared to pool mining via a proxy/VPN/?TOR that adds some latency in the pool mining process?
I think it was a slip up using a traceable account to mount the attacks.
So my guess would be – a C, C++, Java, Assembly Language developer, mid 30s to mid 40s, male, small time miner with the rig small enough to fit in the unit or house, basement or garage, 5 foot 8 inches, long hair :-). And the IP address will point directly to the attacker’s home, but someone will have to get the IP address from DwarfPool and then find out the physical address or owner from the ISP. I don’t know whether the three-letter-acronym agencies would bother. We could set up a prediction event on Augur or Gnosis and place our bets.
The Ethereum Classic And The DAO Hacker Connection
User /u/1dontpanic on the reddit post The Ongoing Ethereum Attacks (Work In Progress) wrote:
It hasn’t come up yet in the thread, but 15 hrs after the attacks finished they dumped into account 0xe9a7e26bf5c05fe3bae272d4c940bd7158611ce9 . This is our public etc dev account, and is not involved with the attack. The funds received will be frozen, same as the dao funds received as far as I’m concerned.
As traced on The Hacker Has Just Withdrawn Their Booty From The DAO On The ETC Chain, The DAO hacker donated 1000 ETCs out from their 3642408.5276 ETC (~ USD 3.7 million) The DAO hack booty to the same Ethereum Classic development account in tx 0x38d8…198b at Sep-05-2016 22:34:13 UTC. This same account was sent ETCs from some of the spam DoS transaction accounts listed above, including 1.7754 ETCs from the account 0xfcd004fbad7e8ffee821d8a10d7f0685b14933b1 in tx 0xd469…1ab9 at Oct-20-2016 12:28:31 UTC.
Coordinated Spam Or Lone Operative
A lone operative could easily have been behind the attack as the sending out of the spam transactions can be easily automated.
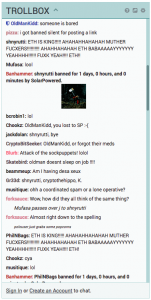
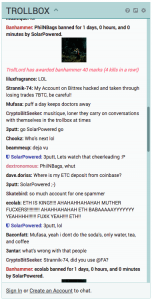
Meanwhile, multiple people were banned for a day from the Polo TrollBox while overexcitedly discussing whether the attacks was the work of “coordinated spam or lone operative”.
 |
 |
 |

Pingback: The DAO Hacker Cashes Out | BitcoinCreative
Pingback: Virtual Mining Bitcoin News » The DAO Hacker Cashes Out
Pingback: The DAO Hacker Cashes Out | Bitcoin & Cryptocurrency
Pingback: The DAO Hacker Cashes Out | New Internet Media
Pingback: The DAO Hacker Cashes Out - One Bitcoin
Pingback: The DAO Hacker Cashes Out - BitcoinEZ
Pingback: Wie die Suche nach einem Hacker eine unbequeme Wahrheit über die Datenschutz-Politik von Shapeshift ans Licht brachte - Coinomia Forum
Pingback: 3 months in ethereum | #Lab