Originally posted Oct 19 2016, updated 02:49 Oct 21 2016 UTC.
Table of contents
- Summary
- The Attacks
- The Hard Forks
- The First Hard Fork – Gas Repricing
- The Attacks Have Stopped
- The Gas Limit
- The Gas Price
- The Uncles
- The Empty Blocks
- A Successful Hard Fork
- The Second Hard Fork – State Clearing
- Ethereum Classic Classic?
- A New Set Of Attacks (Update 14:26 Oct 19 2016 UTC)
- The Good News (Update 22:03 Oct 19 2016 UTC)
Summary
The Gas Reprice hard fork successfully stopped all the previous attacks since the start of Devcon2.
Update 14:26 Oct 19 2016 UTC – The attacker is now conducting a new set of smaller impact attacks using another an underpriced EXP opcode and a BALANCE operation that need some cache improvements – see the updated section at the bottom of this page to see the impact on the block processing. The next planned hard fork will address these new attack vectors – see ATTENTION MINERS: Recommending miners lower the gas limit target to 2 million. What a dynamic and responsive Ethereum ecosystem this is!
Update 02:49 Oct 19 2016 UTC – The attacks have now ceased, at least temporarily. The attacker may have given up as the latest attacks do not have much impact on the running of the network.
And the attacker’s accounts and transactions has ?accidentally? revealed that they pool mined with EthPool and DwarfPool. These pool miners would have recorded the IP address(es) of the attacker’s miners. Read all about it in next exciting blog post Ethereum Network Attacker’s IP Address Is Traceable.
The Attacks
The Ethereum blockchain has been undergoing a attack since the start of the Devcon2 conference a few weeks ago (beginning Sep 19 2016).
The first attack started on block 2,283,416 at 01:04:56 Sep 19 Shanghai time and targeted the go-ethereum geth clients, causing a memory error and shutting down these nodes across the network. Luckily the Ethereum network has separately implemented node clients written in Rust (Parity) and Java (EthereumJ) – these clients did not suffer from the same memory bug and kept the network up and running. The Ethereum developers in Shanghai had to get up early before the start of the conference and shortly after released a version of geth with the memory bug fixed. This ended up delaying the start of the conference by half an hour.
My 125 Mhs solo miner stopped working for the week while I was in Shanghai as I had not set up a VPN connection to my node due to security reasons.
Soon after the first attack, the attacker then regularly sent spam transactions (see here and here) to slow down the Ethereum network. Using cheaply priced opcodes (Ethereum Virtual Machine instruction codes), the attacker sent transactions that caused heavy computational and disk input/output loads on the Ethereum nodes. This was later followed by spam transactions that created many empty accounts on the blockchain, causing a “state-bloat” on the blockchain.
Worst affected users seem to be those trying to run a full sync of the Ethereum blockchain on machines with limited memory and running on a hard disk drive (HDD) instead of a solid state drive (SSD). See Is something wrong with the network right now?, sync isn’t working for 0.8.5 been trying for days and 5th time downloading Blockchain 15 days for example.
Non-spam transactions were failing as quite a number of mining pools decided not to process transactions as these would slow down their mining node operations, and the non-spam transactions were getting lost in the ether.
The Hard Forks
The Ethereum Foundation announced two hard forks to stop the spam transaction attacks. As listed in the previous link, you have to install the latest Ethereum node clients containing the hard fork code – geth 1.4.18, Parity 1.3.8, EthereumJ 1.3.6 and Ethereum Wallet 0.8.6 (remember never to trust links to the node clients from unofficial sites). If you have run an earlier version of the node client after the first Gas Repricing hard fork (see below), you will have to re-sync your blockchain data from scratch.
The First Hard Fork – Gas Repricing
The first EIP 150 Long-term gas cost changes for IO-heavy operations to mitigate transaction spam attacks hard fork successfully activated at block 2,463,000 at Oct-18-2016 01:19:31 PM +UTC to reprice the gas for some of the opcodes. This raises the cost for the attacker to send their spam transactions.
The Attacks Have Stopped
The attackers transactions started failing (source) immediately after the hard fork. This account spend 9 – 3.899521491 = 5.100478509 ethers (~ USD 64.10) to send 1,183 spam transactions to the network.
The Gas Limit
The gasLimit represents the total amount of gas for the computation and storage that can be spent within each block (14 seconds average block time). This gasLimit is a figure that is voted on by the miners.
You can see the Gas Limit chart increasing on the bottom right of the chart below from https://ethstats.net/ around 7+ hours after the hard fork:
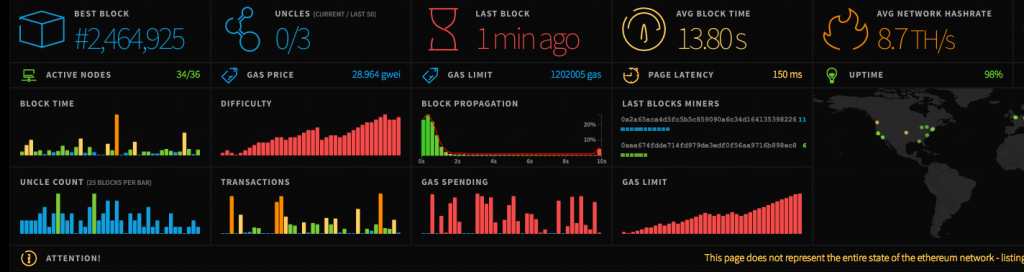
Following are some gasLimit statistics. The gasLimit was around 4.7 million before the attack. As advised by the Ethereum Foundation, miners voted to reduce the gasLimit to 1.5 million during the attack to limit the damage by the spam transactions, and this was reduced further to 0.5 million at the later stages of the attack. You can now see it rising to 2.5 million:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 |
function checkAverageGasLimitEvery1000Blocks(lookback) { var gasLimit = new BigNumber(0); var i; var currentBlockNumber = eth.blockNumber - lookback; for (i = -10000; i < 0; i++) { var blockNumber = currentBlockNumber + i; gasLimit = gasLimit.plus(eth.getBlock(blockNumber).gasLimit); if ((i % 1000) == 0 && i != -10000) { var d = eth.getBlock(blockNumber).timestamp; gasLimit = gasLimit.div(1000); console.log(blockNumber + "\t" + new Date(d*1000).toUTCString() + "\t" + gasLimit); gasLimit = new BigNumber(0); } } } > checkAverageGasLimitEvery1000Blocks(300000); 2157994 Sun, 28 Aug 2016 23:43:06 UTC 4713346.869 2158994 Mon, 29 Aug 2016 03:42:56 UTC 4708939.88 2159994 Mon, 29 Aug 2016 07:45:02 UTC 4708287.85 2160994 Mon, 29 Aug 2016 11:47:34 UTC 4708316.478 2161994 Mon, 29 Aug 2016 15:45:58 UTC 4708676.895 2162994 Mon, 29 Aug 2016 19:44:51 UTC 4708325.929 2163994 Mon, 29 Aug 2016 23:41:52 UTC 4708421.299 2164994 Tue, 30 Aug 2016 03:39:10 UTC 4708152.03 2165994 Tue, 30 Aug 2016 07:37:07 UTC 4708272.041 undefined > checkAverageGasLimitEvery1000Blocks(200000); 2258001 Wed, 14 Sep 2016 13:03:23 UTC 4712840.524 2259001 Wed, 14 Sep 2016 17:05:52 UTC 4707779.419 2260001 Wed, 14 Sep 2016 21:08:15 UTC 4708353.49 2261001 Thu, 15 Sep 2016 00:59:21 UTC 4708248.539 2262001 Thu, 15 Sep 2016 04:56:43 UTC 4708533.085 2263001 Thu, 15 Sep 2016 09:00:54 UTC 4708003.432 2264001 Thu, 15 Sep 2016 12:52:07 UTC 4708592.725 2265001 Thu, 15 Sep 2016 16:52:07 UTC 4708319.255 2266001 Thu, 15 Sep 2016 20:47:42 UTC 4707937.816 // Before attacks undefined > checkAverageGasLimitEvery1000Blocks(100000); 2358012 Sat, 01 Oct 2016 02:37:44 UTC 1501264.782 // During attacks 2359012 Sat, 01 Oct 2016 06:55:32 UTC 1499817.045 2360012 Sat, 01 Oct 2016 11:03:35 UTC 1499651.46 2361012 Sat, 01 Oct 2016 15:00:01 UTC 1499774.121 2362012 Sat, 01 Oct 2016 19:22:49 UTC 1499995.815 2363012 Sat, 01 Oct 2016 23:23:05 UTC 1499963.672 2364012 Sun, 02 Oct 2016 03:17:53 UTC 1499896.736 2365012 Sun, 02 Oct 2016 07:12:16 UTC 1498932.193 2366012 Sun, 02 Oct 2016 11:09:21 UTC 1498849.484 undefined > checkAverageGasLimitEvery1000Blocks(0); 2458027 Mon, 17 Oct 2016 17:23:05 UTC 500720.531 2459027 Mon, 17 Oct 2016 21:27:48 UTC 500262.692 2460027 Tue, 18 Oct 2016 01:33:09 UTC 500222.285 2461027 Tue, 18 Oct 2016 05:34:28 UTC 500228.19 2462027 Tue, 18 Oct 2016 09:30:42 UTC 500262.456 2463027 Tue, 18 Oct 2016 13:27:42 UTC 500266.979 // Just after hard fork 2464027 Tue, 18 Oct 2016 17:18:08 UTC 617823.939 2465027 Tue, 18 Oct 2016 21:14:26 UTC 1000341.647 2466027 Wed, 19 Oct 2016 01:04:48 UTC 1493273.24 undefined > console.log(new Date().toUTCString() + "\tblockNumber=" + eth.getBlock("latest").number + "\tgasLimit=" + eth.getBlock("latest").gasLimit) Wed, 19 Oct 2016 05:03:08 UTC blockNumber=2467038 gasLimit=2541509 |
The Gas Price
The gasPrice increased during the attacks as a portion of miners stopped accepting transactions and the remaining miners that accepted transactions had their blocks full from the spam transactions. Non-spam transactions were getting dropped and unprocessed by the Ethereum network. For non-spam transactions to be mined, the gasPrice for these transactions had to be increased. From https://etherscan.io/charts/gasprice:
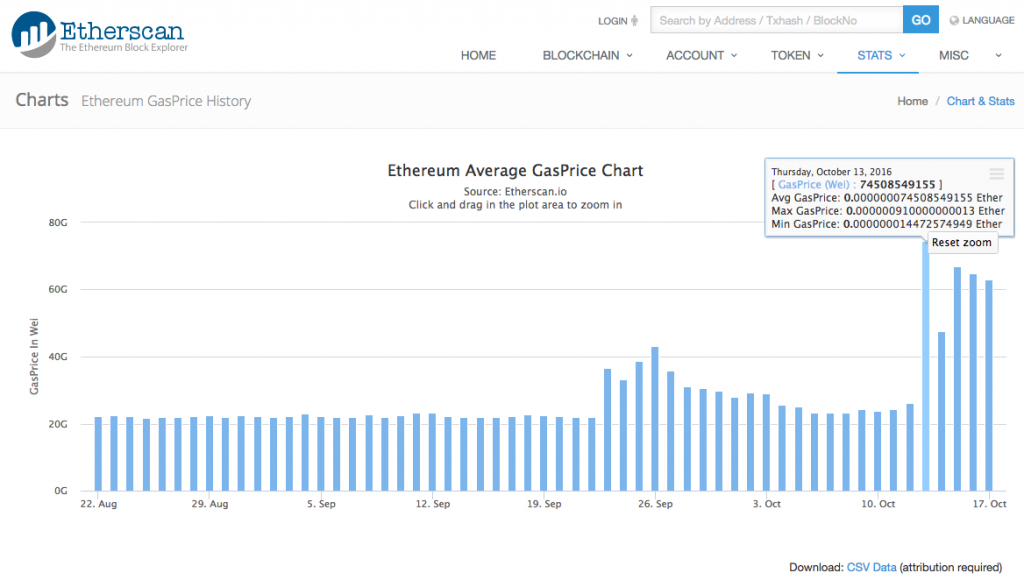
Checking the current gasPrice with the following code, the gasPrice has fallen back to the pre-attack levels:
|
1 2 |
> console.log(new Date().toUTCString() + "\t" + web3.fromWei(eth.gasPrice, "wei") + " wei =" + web3.fromWei(eth.gasPrice, "ether").toFixed(9) + " ETH"); Wed, 19 Oct 2016 04:40:42 UTC 20000000000 wei =0.000000020 ETH |
Regular account to account transactions cost 21,000 gas, which now equates to around 0.000459187432998 ETH or ~ USD 0.005365596876048108, or around half a cent, at 1 ETH = 12.543 USD. At the peak, someone paid a gasPrice of 0.00000091, ~ 45x the normal amount, to push their transactions through the network.
The Uncles
The rate of uncles per 1,000 blocks has been higher than average during the attack period but this is now falling:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 |
function checkUnclesEvery1000Blocks(lookback) { var uncles = 0; var i; var currentBlockNumber = eth.blockNumber - lookback; for (i = -10000; i < 0; i++) { var blockNumber = currentBlockNumber + i; uncles += eth.getBlockUncleCount(blockNumber); if ((i % 1000) == 0 && i != -10000) { var d = eth.getBlock(blockNumber).timestamp; console.log(blockNumber + "\t" + new Date(d*1000).toUTCString() + "\t" + uncles); uncles = 0; } } } > checkUnclesEvery1000Blocks(300000); 2157956 Sun, 28 Aug 2016 23:34:05 UTC 82 2158956 Mon, 29 Aug 2016 03:32:53 UTC 80 2159956 Mon, 29 Aug 2016 07:36:15 UTC 87 2160956 Mon, 29 Aug 2016 11:39:24 UTC 74 2161956 Mon, 29 Aug 2016 15:38:41 UTC 79 2162956 Mon, 29 Aug 2016 19:36:45 UTC 70 2163956 Mon, 29 Aug 2016 23:33:04 UTC 71 2164956 Tue, 30 Aug 2016 03:31:21 UTC 83 2165956 Tue, 30 Aug 2016 07:27:07 UTC 78 undefined > checkUnclesEvery1000Blocks(200000); 2257957 Wed, 14 Sep 2016 12:53:35 UTC 104 2258957 Wed, 14 Sep 2016 16:56:11 UTC 85 2259957 Wed, 14 Sep 2016 20:56:28 UTC 74 2260957 Thu, 15 Sep 2016 00:48:40 UTC 87 2261957 Thu, 15 Sep 2016 04:45:09 UTC 89 2262957 Thu, 15 Sep 2016 08:52:12 UTC 82 2263957 Thu, 15 Sep 2016 12:43:48 UTC 73 2264957 Thu, 15 Sep 2016 16:42:10 UTC 90 2265957 Thu, 15 Sep 2016 20:40:12 UTC 99 // Before attacks undefined > checkUnclesEvery1000Blocks(100000); 2357957 Sat, 01 Oct 2016 02:22:16 UTC 118 // During attacks 2358957 Sat, 01 Oct 2016 06:40:46 UTC 299 2359957 Sat, 01 Oct 2016 10:50:06 UTC 186 2360957 Sat, 01 Oct 2016 14:46:25 UTC 267 2361957 Sat, 01 Oct 2016 19:08:04 UTC 302 2362957 Sat, 01 Oct 2016 23:10:05 UTC 304 2363957 Sun, 02 Oct 2016 03:05:49 UTC 285 2364957 Sun, 02 Oct 2016 07:01:00 UTC 243 2365957 Sun, 02 Oct 2016 10:52:56 UTC 235 undefined > checkUnclesEvery1000Blocks(0); 2457960 Mon, 17 Oct 2016 17:08:27 UTC 85 2458960 Mon, 17 Oct 2016 21:11:54 UTC 106 2459960 Tue, 18 Oct 2016 01:11:26 UTC 127 2460960 Tue, 18 Oct 2016 05:19:24 UTC 132 2461960 Tue, 18 Oct 2016 09:11:13 UTC 178 2462960 Tue, 18 Oct 2016 13:11:06 UTC 142 2463960 Tue, 18 Oct 2016 17:00:59 UTC 96 // After hard fork 2464960 Tue, 18 Oct 2016 20:53:43 UTC 92 2465960 Wed, 19 Oct 2016 00:49:29 UTC 89 undefined |
The higher than average rate of uncles during the attack period was most likely due to mining nodes being slowed down by the heavy computational and disk input/output burden caused by the spam transactions.
The Empty Blocks
During the attack, some miners decided not to include any transactions in their mined blocks as processing these transactions would slow down the initial preparation of the block before mining on the block commences – see Dwarfpool Empty Block Mining? and Wall of fame / wall of shame – miners who are doing nothing for the network right now. Here are some statistics that show that empty blocks have not yet reduced to the pre-attack period:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 |
function checkEmptyBlocks(lookback) { var emptyBlocks = 0; var i; var currentBlockNumber = eth.blockNumber - lookback; for (i = -10000; i < 0; i++) { var blockNumber = currentBlockNumber + i; if (eth.getBlockTransactionCount(blockNumber) == 0) { emptyBlocks++; } if ((i % 1000) == 0 && i != -10000) { var d = eth.getBlock(blockNumber).timestamp; console.log(blockNumber + "\t" + new Date(d*1000).toUTCString() + "\t" + emptyBlocks); emptyBlocks = 0; } } } > checkEmptyBlocks(300000); 2157940 Sun, 28 Aug 2016 23:31:07 UTC 349 2158940 Mon, 29 Aug 2016 03:28:49 UTC 371 2159940 Mon, 29 Aug 2016 07:31:53 UTC 342 2160940 Mon, 29 Aug 2016 11:36:51 UTC 310 2161940 Mon, 29 Aug 2016 15:35:04 UTC 322 2162940 Mon, 29 Aug 2016 19:31:39 UTC 296 2163940 Mon, 29 Aug 2016 23:27:06 UTC 328 2164940 Tue, 30 Aug 2016 03:27:35 UTC 366 2165940 Tue, 30 Aug 2016 07:23:52 UTC 339 undefined > checkEmptyBlocks(200000); 2257943 Wed, 14 Sep 2016 12:50:38 UTC 169 2258943 Wed, 14 Sep 2016 16:53:22 UTC 173 2259943 Wed, 14 Sep 2016 20:51:47 UTC 228 2260943 Thu, 15 Sep 2016 00:46:35 UTC 317 2261943 Thu, 15 Sep 2016 04:42:50 UTC 352 2262943 Thu, 15 Sep 2016 08:49:47 UTC 178 2263943 Thu, 15 Sep 2016 12:40:43 UTC 240 2264943 Thu, 15 Sep 2016 16:38:55 UTC 180 2265943 Thu, 15 Sep 2016 20:36:42 UTC 203 // Before attacks undefined > checkEmptyBlocks(100000); 2357946 Sat, 01 Oct 2016 02:20:30 UTC 451 // During attacks 2358946 Sat, 01 Oct 2016 06:37:36 UTC 440 2359946 Sat, 01 Oct 2016 10:46:48 UTC 438 2360946 Sat, 01 Oct 2016 14:43:29 UTC 449 2361946 Sat, 01 Oct 2016 19:06:09 UTC 426 2362946 Sat, 01 Oct 2016 23:08:16 UTC 379 2363946 Sun, 02 Oct 2016 03:04:02 UTC 409 2364946 Sun, 02 Oct 2016 06:58:24 UTC 512 2365946 Sun, 02 Oct 2016 10:50:42 UTC 523 undefined > checkEmptyBlocks(0); 2457950 Mon, 17 Oct 2016 17:06:56 UTC 367 2458950 Mon, 17 Oct 2016 21:08:17 UTC 346 2459950 Tue, 18 Oct 2016 01:10:13 UTC 345 2460950 Tue, 18 Oct 2016 05:16:15 UTC 296 2461950 Tue, 18 Oct 2016 09:09:23 UTC 268 2462950 Tue, 18 Oct 2016 13:09:30 UTC 348 2463950 Tue, 18 Oct 2016 16:57:53 UTC 352 // After hard fork 2464950 Tue, 18 Oct 2016 20:52:32 UTC 332 2465950 Wed, 19 Oct 2016 00:47:23 UTC 343 undefined |
A Successful Hard Fork
Congratulations to the developers and the Ethereum Foundation for a successful hard fork! The spam transactions have stopped. For a while at least. Update 14:26 Oct 19 2016 UTC – Less than a day of calm.
The Second Hard Fork – State Clearing
There will be the EIP #158 State Clearing hard fork shortly to remove many of the empty accounts filling up the blockchain.
Ethereum Classic Classic?
This gas repricing hard fork was not as contentious as the hard fork to refund the USD 50 million hack on The DAO’s smart contract code with a bug. The Ethereum Classic (ETC) chain arose from this The DAO hard fork as about 10% of miners (who insist on immutable blockchains) continued mining on the non-hard forked chain. And the It-Who-Must-Not-Be-Named exchange listed ETC on their exchange by surprise.
The ETC chain has recently been undergoing similar spam transaction attack and there is a proposal to perform the same hard fork at block 2,500,000 on Oct 25 2016. As this hard fork violates the principle of an immutable blockchain that is a concern for some part of that community, there are calls for a vote before hard forking. There is a small chance that an Ethereum Classic Classic (ETCC) chain may arise from this community split.
A New Set Of Attacks (Update 14:26 Oct 19 2016 UTC)
A new set of attacks using underpriced EXP and BALANCE opcodes is currently occurring – see Lol, I think its another attack contract – Burns fees like a champ. Somone is very persistent here 🙂. The effects on the network are apparently not severe like the previous attacks. And this opcode will be repriced in the next hard fork.
The following logs shows that some blocks are taking longer than usual to process.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 |
// geth running on my Macbook Air - up to 10 seconds to process some blocks I1020 00:32:51.043543 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 20 txs in 9.659660949s. #2469043 [a8e83598 / a8e83598] I1020 00:32:56.462486 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 12 txs in 5.413096939s. #2469044 [7539f516 / 7539f516] I1020 00:32:59.294688 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 1 txs in 7.572923ms. #2469043 [43159825 / 43159825] I1020 00:33:05.819443 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 10.632415ms. #2469045 [75e40371 / 75e40371] I1020 00:33:32.557822 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 12 txs in 9.489027618s. #2469046 [46bf1869 / 46bf1869] I1020 00:33:44.212843 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 4 txs in 12.276909ms. #2469047 [f482688b / f482688b] I1020 00:34:18.885343 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 12 txs in 10.215295819s. #2469048 [858c89fa / 858c89fa] I1020 00:34:18.895052 core/blockchain.go:1001] imported 1 block(s) (0 queued 1 ignored) including 13 txs in 9.654351ms. #2469049 [858c89fa / 78704291] I1020 00:34:29.303799 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 13 txs in 9.512011695s. #2469050 [1b7f7c43 / 1b7f7c43] I1020 00:34:30.187835 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 6.495512ms. #2469050 [42ba6725 / 42ba6725] I1020 00:34:42.538841 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 7.477749ms. #2469051 [4af0e2eb / 4af0e2eb] I1020 00:35:43.635580 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 14 txs in 9.289186837s. #2469052 [d84ff7c8 / d84ff7c8] I1020 00:35:56.769851 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 18 txs in 23.218423ms. #2469053 [8501f360 / 8501f360] I1020 00:36:17.192551 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 1 txs in 6.326109ms. #2469054 [99f4c275 / 99f4c275] I1020 00:36:18.457158 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 5.390568ms. #2469055 [2d9b05bf / 2d9b05bf] // Parity running on my virtual server - up to 5 seconds to process some blocks 2016-10-20 00:32:43 Imported #2469043 a8e8…5f46 (20 txs, 3.89 Mgas, 4705.67 ms, 3.13 KiB) 2016-10-20 00:32:51 Imported #2469044 7539…b210 (12 txs, 3.68 Mgas, 2941.12 ms, 2.07 KiB) 2016-10-20 00:32:52 0/48/50 peers 19 MiB db 5 MiB chain 2 KiB queue 456 KiB sync 2016-10-20 00:32:56 Imported #2469043 4315…e913 (1 txs, 0.02 Mgas, 1.46 ms, 0.63 KiB) 2016-10-20 00:33:04 Imported #2469045 75e4…862a (0 txs, 0.00 Mgas, 1.67 ms, 1.04 KiB) 2016-10-20 00:33:23 1/48/50 peers 19 MiB db 5 MiB chain 2 KiB queue 457 KiB sync 2016-10-20 00:33:26 Imported #2469046 46bf…fed6 (12 txs, 3.60 Mgas, 2772.87 ms, 2.01 KiB) 2016-10-20 00:33:43 Imported #2469047 f482…905a (4 txs, 1.71 Mgas, 6.98 ms, 6.81 KiB) 2016-10-20 00:33:53 0/48/50 peers 19 MiB db 5 MiB chain 2 KiB queue 456 KiB sync 2016-10-20 00:34:11 Imported #2469048 858c…9920 (12 txs, 3.60 Mgas, 5034.20 ms, 2.01 KiB) 2016-10-20 00:34:21 Imported #2469050 1b7f…708d (13 txs, 3.83 Mgas, 4225.16 ms, 2.60 KiB) + another 1 block(s) 2016-10-20 00:34:24 0/48/50 peers 18 MiB db 5 MiB chain 2 KiB queue 456 KiB sync 2016-10-20 00:34:30 Imported #2469050 42ba…84af (0 txs, 0.00 Mgas, 0.78 ms, 0.52 KiB) 2016-10-20 00:34:41 Reorg to #2469051 4af0…8d1d (1b7f…708d #2469049 7870…6a96 42ba…84af) 2016-10-20 00:34:41 Imported #2469051 4af0…8d1d (0 txs, 0.00 Mgas, 1.91 ms, 0.52 KiB) 2016-10-20 00:34:54 0/48/50 peers 18 MiB db 5 MiB chain 2 KiB queue 456 KiB sync 2016-10-20 00:35:25 0/48/50 peers 18 MiB db 5 MiB chain 2 KiB queue 456 KiB sync 2016-10-20 00:35:31 Imported #2469052 d84f…ca1e (14 txs, 3.85 Mgas, 27.73 ms, 3.22 KiB) 2016-10-20 00:35:55 0/48/50 peers 18 MiB db 5 MiB chain 2 KiB queue 456 KiB sync 2016-10-20 00:35:56 Imported #2469053 8501…bd7d (18 txs, 0.58 Mgas, 15.98 ms, 3.08 KiB) 2016-10-20 00:36:15 Imported #2469054 99f4…4599 (1 txs, 0.50 Mgas, 2.90 ms, 2.58 KiB) 2016-10-20 00:36:17 Imported #2469055 2d9b…d161 (0 txs, 0.00 Mgas, 0.98 ms, 0.51 KiB) 2016-10-20 00:36:25 0/48/50 peers 18 MiB db 5 MiB chain 2 KiB queue 456 KiB sync // geth running on my solo mining node with a low specced CPU - up to 33 seconds to process some blocks I1020 00:32:42.742227 miner/worker.go:539] commit new work on block 2469043 with 23 txs & 0 uncles. Took 1.0199364s I1020 00:33:10.390468 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 20 txs in 28.733235855s. #2469043 [a8e83598 / a8e83598] I1020 00:33:10.919816 miner/worker.go:539] commit new work on block 2469044 with 23 txs & 0 uncles. Took 524.684959ms I1020 00:33:22.418526 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 12 txs in 12.024350639s. #2469044 [7539f516 / 7539f516] I1020 00:33:22.423112 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 1 txs in 4.542614ms. #2469043 [43159825 / 43159825] I1020 00:33:22.434671 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 7.698511ms. #2469045 [75e40371 / 75e40371] I1020 00:33:27.477946 miner/worker.go:539] commit new work on block 2469045 with 21 txs & 0 uncles. Took 5.058014449s I1020 00:33:28.785764 miner/worker.go:539] commit new work on block 2469046 with 23 txs & 0 uncles. Took 1.307781816s I1020 00:33:55.654967 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 12 txs in 32.302568264s. #2469046 [46bf1869 / 46bf1869] I1020 00:33:55.668998 core/blockchain.go:1001] imported 1 block(s) (0 queued 1 ignored) including 16 txs in 13.97417ms. #2469047 [46bf1869 / f482688b] I1020 00:34:00.345290 miner/worker.go:539] commit new work on block 2469047 with 20 txs & 0 uncles. Took 4.684836742s I1020 00:34:05.221332 miner/worker.go:539] commit new work on block 2469048 with 19 txs & 0 uncles. Took 4.876006493s I1020 00:34:43.495964 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 12 txs in 33.090771592s. #2469048 [858c89fa / 858c89fa] I1020 00:34:43.506047 core/blockchain.go:1001] imported 1 block(s) (0 queued 1 ignored) including 13 txs in 10.04303ms. #2469049 [858c89fa / 78704291] I1020 00:34:43.518285 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 4.48897ms. #2469050 [42ba6725 / 42ba6725] I1020 00:34:48.324418 miner/worker.go:539] commit new work on block 2469049 with 21 txs & 0 uncles. Took 4.823874484s I1020 00:34:53.599232 miner/worker.go:539] commit new work on block 2469051 with 20 txs & 0 uncles. Took 5.27477654s I1020 00:34:55.195663 miner/worker.go:539] commit new work on block 2469051 with 20 txs & 0 uncles. Took 1.596398023s I1020 00:35:08.630286 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 13 txs in 25.111965254s. #2469050 [1b7f7c43 / 1b7f7c43] I1020 00:35:08.635657 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 5.339419ms. #2469051 [4af0e2eb / 4af0e2eb] I1020 00:35:08.709391 miner/worker.go:539] commit new work on block 2469051 with 20 txs & 1 uncles. Took 76.987443ms I1020 00:35:10.302185 miner/worker.go:539] commit new work on block 2469052 with 20 txs & 1 uncles. Took 1.592757807s I1020 00:35:36.499455 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 14 txs in 4.071344935s. #2469052 [d84ff7c8 / d84ff7c8] I1020 00:35:41.447543 miner/worker.go:539] commit new work on block 2469053 with 38 txs & 0 uncles. Took 4.948034828s I1020 00:35:56.948980 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 18 txs in 27.221715ms. #2469053 [8501f360 / 8501f360] I1020 00:36:01.533511 miner/worker.go:539] commit new work on block 2469054 with 24 txs & 0 uncles. Took 4.584313659s I1020 00:36:15.011064 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 1 txs in 5.777414ms. #2469054 [99f4c275 / 99f4c275] I1020 00:36:17.803840 core/blockchain.go:1001] imported 1 block(s) (0 queued 0 ignored) including 0 txs in 5.008621ms. #2469055 [2d9b05bf / 2d9b05bf] I1020 00:36:20.096527 miner/worker.go:539] commit new work on block 2469055 with 25 txs & 0 uncles. Took 5.084118022s |
Update 09:13 Oct 20 2016 UTC – From FAQ: Upcoming Ethereum Hard Fork – Ethereum Blog, vitalik stated before the new attacks that:
It’s worth noting that an increase in the gas cost of the EXP opcode is likely in HF round 2; this is the one arithmetic opcode that we’ve found that is underpriced (though by a substantially smaller factor than what’s getting fixed in HF round 1).
The Good News (Update 22:03 Oct 19 2016 UTC)
From Lol, I think its another attack contract – Burns fees like a champ. Somone is very persistent here 🙂, gustav_simonsson writes:
Correcting the gas cost of op codes makes Ethereum more efficient as it enables more txs and real throughput by disincentivizing “artificial” use of the platform – simple loops over op codes which has no utility other than DoS.
In fact, the attack surface of Ethereum is surprisingly small given that it’s much more powerful & flexible than other live blockchain systems. This is much due to having cross-client specifications & test suits and multiple implementations in different programming languages.
Claiming the attacker has “unlimited runway to continue” is ignorant FUD.
The vulnerabilities fixed over the past weeks have all been in very specific subsets of the Ethereum protocols:
1. gas cost of a subset of the VM op codes.
2. logic around “empty” accounts
3. performance of state handling of accounts.
4. unconfirmed tx (mempool) queuing & broadcast logic.(3) and (4) have been vastly improved in geth, parity and other implementations which is why the attacker is no longer targeting these.
(1) was too a large degree fixed by the HF, although it’s clear that EXP (and possibly a few other arithmetic op codes) also need to be adjusted.
(1) and (2) will be further addressed by a 2nd HF (https://github.com/ethereum/EIPs/issues/158)
With the current gas system, there will always be some combination of op codes requiring the most resource usage for the least cost.
Prior to this HF, the block gas limit was voted to 0.5M to ensure the network remained operational and processed txs during attacks.
Now we see that the network is chugging along during attack txs with a at 2M gas limit (although older, slower systems without SSD drives will need patches that are currently being worked on in both geth and parity).
Overall, this HF + patches in clients have improved the bottleneck of Ethereum by more than an order of magnitude. In a few weeks, it’ll be another order of magnitude.
And in the long term all txs we currently describe as “attack” or “DoS” txs will become indistinguishable from regular txs as their tx fees will be proportional to their resource usage.
